如何修復 Intel ME 後門 (for Ubuntu)
話說最近的 Intel 後門把大家搞的雞飛狗跳,小獅我也來跟個風,整理了相關的 2 個漏洞資訊,方便同為 Linux 使用者的各位,檢查一下自己該怎麼解決這個問題。
Step 0. 我有後門嗎?
如何知道我的電腦上有沒有 Intel Management Engine
根據 Debian wiki:
lspci | egrep '(MEI|HECI)'
我的執行果:
~ lspci | egrep '(MEI|HECI)' 00:16.0 Communication controller: Intel Corporation 8 Series/C220 Series Chipset Family MEI Controller #1 (rev 04)
Intel SA-00075
Intel 官方聲明:
On May 1, Intel published a security advisory regarding a critical firmware vulnerability in certain systems that utilize Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM) or Intel® Small Business Technology (SBT). The vulnerability could enable a network attacker to remotely gain access to business PCs or devices that use these technologies. Consumer PCs with consumer firmware and data center servers using Intel® Server Platform Services are not affected by this vulnerability.
受影響的 CPU 清單(SA-00075):
| ME 韌體版本 | CPU 世代 | 已修正的韌體 |
|---|---|---|
| 6.0.xx.xxxx | 1st Gen Core | 6.2.61.3535 |
| 6.1.xx.xxxx | 6.2.61.3535 | |
| 6.2.xx.xxxx | 6.2.61.3535 | |
| 7.0.xx.xxxx | 2nd Gen Core | 7.1.91.3272 |
| 7.1.91.3272 | 7.1.91.3272 | |
| 8.0.xx.xxxx | 3rd Gen Core | 8.1.71.3608 |
| 8.1.xx.xxxx | 8.1.71.3608 | |
| 9.0.xx.xxxx | 4th Gen Core | 9.1.41.3024 |
| 9.1.xx.xxxx | 9.1.41.3024 | |
| 9.5.xx.xxxx | 9.5.61.3012 | |
| 10.0.xx.xxxx | 5th Gen Core | 10.0.55.3000 |
| 10.0.xx.xxxx | 5th Gen Core | 10.0.55.3000 |
| 11.0.xx.xxxx | 6th Gen Core | 11.0.25.3001 |
| 11.0.22.3001 | ||
| 11.0.18.3003 | ||
| 11.5.xx.xxxx | 7th Gen Core | 11.6.27.3264 |
| 11.6.xx.xxxx | 11.6.27.3264 | |
| 11.6.12.3202 |
(資料來源:Intel Security Center)
官方偵測工具(Link)
Intel SA-00086
根據官方的安全建議,受影響的 CPU 包括:
- 6th, 7th & 8th Generation Intel® Core™ Processor Family
- Intel® Xeon® Processor E3-1200 v5 & v6 Product Family
- Intel® Xeon® Processor Scalable Family
- Intel® Xeon® Processor W Family
- Intel® Atom® C3000 Processor Family
- Apollo Lake Intel® Atom Processor E3900 series
- Apollo Lake Intel® Pentium™
- Celeron™ N and J series Processors
官方偵測工具(Link)
Step 1. 檢查 ME 版本是否受影響
根據上面的 2 個清單,簡單來說,所有的 Core i 系列、所有的 Xeon E3、所有的 Atom C 系列 都在可能的受影響名單之中
Intel SA-00075
所以根據剛才出現過得那一篇聲明,我們可以在這裡找到一個修復指南(Mitigation Guide),但顯然只是個下載連結,而且還沒有提供 Linux 板…
沒關係,我們跟著連結繼續追下去,找到了這東西 照著說明做完之後會得到一份報告
git clone https://github.com/intel/INTEL-SA-00075-Linux-Detection-And-Mitigation-Tools.git cd INTEL-SA-00075-Linux-Detection-And-Mitigation-Tools make # 編譯失敗的話先下 sudo apt install build-essential 再試一次
報告:
> sudo ./INTEL-SA-00075-Discovery-Tool -d /dev/mei0 INTEL-SA-00075-Discovery-Tool -- Release 1.0 Copyright (C) 2003-2012, 2017 Intel Corporation. All rights reserved 略... ------------------Vulnerability Status-------------------- Based on the version of the Intel(R) MEI, the System is Vulnerable. If Vulnerable, contact your OEM for support and remediation of this system. For more information, refer to CVE-2017-5689 at: https://nvd.nist.gov/vuln/detail/CVE-2017-5689 or the Intel security advisory Intel-SA-00075 at: https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00075&languageid=en-fr ----------------------------------------------------------
修復工具:
> sudo ./INTEL-SA-00075-Unprovisioning-Tool -d /dev/mei0 INTEL-SA-00075-Unprovisioning-Tool -- Release 1.0 Copyright (C) 2003-2012, 2017 Intel Corporation. All rights reserved ----------------------------------------------------------- PROVISIONING_STATE = PRE System is in unprovisioned state. Exiting. ----------------------------------------------------------
成功的話應該就會看到 Successfully Un-provisioned 訊息,但是小獅我忘記截圖了 Orz…
注: 歲然 GitHub 頁面上有 “最新版本” 的下載連結,但經過我的測試其實版本比較舊
~/Downloads md5sum INTEL-SA-00075-Linux-Detection-And-Mitigation-Tools-v1.2.zip 2d043001f4eacea6b2cdcc646394fe6a INTEL-SA-00075-Linux-Detection-And-Mitigation-Tools-v1.2.zip ~/Downloads cd INTEL-SA-00075-Linux-Detection-And-Mitigation-Tools-v1.2/tools ~/Downloads/INTEL-SA-00075-Linux-Detection-And-Mitigation-Tools-v1.2/tools sudo ./INTEL-SA-00075-Discovery-Tool -d /dev/mei0 INTEL-SA-00075-Discovery-Tool -- Release 0.8 Copyright (C) 2003-2012, 2017 Intel Corporation. All rights reserved 略
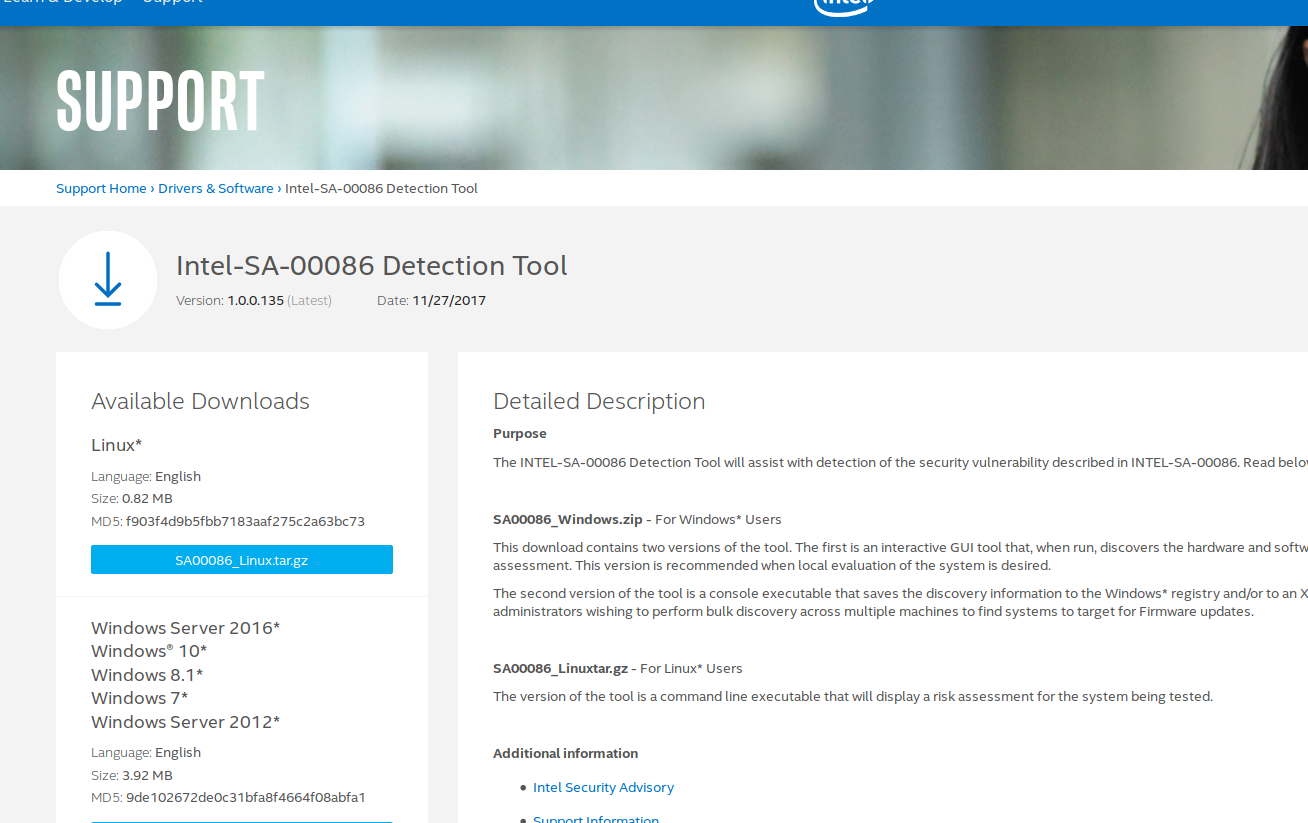
Intel SA-00086
首先請到這個網頁下載檢測工具:
※ 因為需要同意使用者授權合約,請務必使用覽器下載 ※
# 檢查一下 MD5 md5sum SA00086_Linux.tar.gz # f903f4d9b5fbb7183aaf275c2a63bc73 # 解壓縮 mkdir /tmp/0086 tar -C /tmp/0086 -xvf SA00086_Linux.tar.gz cd /tmp/0086 # 設定權限 chmod +x intel_sa00086.py spsInfoLinux64
執行:
> sudo ./intel_sa00086.py INTEL-SA-00086 Detection Tool Copyright(C) 2017, Intel Corporation, All rights reserved Application Version: 1.0.0.135 Scan date: 2017-11-30 12:40:07 GMT *** Host Computer Information *** Name: 231-10 Manufacturer: ASUSTeK COMPUTER INC. Model: BM1AF_BP1AF_BM6AF Processor Name: Intel(R) Core(TM) i5-4590 CPU @ 3.30GHz OS Version: Ubuntu 17.04 zesty (4.10.0-40-generic) *** Intel(R) ME Information *** Engine: Intel(R) Management Engine Version: 9.1.2.1010 SVN: 0 *** Risk Assessment *** Based on the analysis performed by this tool: This system is not vulnerable. For more information refer to the INTEL-SA-00086 Detection Tool Guide or the Intel Security Advisory Intel-SA-00086 at the following link: https://www.intel.com/sa-00086-support
如果出現 the System is Vulnerable 的訊息,就目前情況看來,請 自求多福 致電系統提供商(ex. ASUS, MSI)
就算你看到這裡,已經決定不再相信 Intel,但你至少可以參考一下他們整理的支援清單…
目前的解法不外乎是更新 BOIS 或韌體更新(假設你正在使用 NAS)。
後記
總之這次火燒得很旺,我也被燒到了… 先去療傷 Orz
Ps. 華碩在這次的反應居然比 MSI、Gigabyte 還慢,看來我真的得發 Ticket 問問了…
▲ 最新板? Really?
參考資料
- PSA: Remember To Update Your Intel Management Engine
- 讓Intel 第 6、7、8代Core i處理器都陷入資安漏洞,詳解 Intel ME到底是什麼? | T客邦 – 我只推薦好東西
- Intel® Product Security Center (INTEL-SA-00086)
- Intel® Management Engine Critical Firmware Update (Intel-SA-00086)
- Download INTEL-SA-00075 Detection and Mitigation Tool
- Download INTEL-SA-00075 Linux* Detection and Mitigation Tools
- intel/INTEL-SA-00075-Linux-Detection-And-Mitigation-Tools – GitHub
Intel Logo 的照片來自 Josh Bancroft (CC BY-NC 2.0)


![[Linux] 如何使用 LUKS 建立加密的磁碟映像檔](https://img.alexleo.click/Team-BoB_luks_disk_image/pixy.org_97715-small.jpg)
![[筆記] Matplotlib 使用上的一些建議](https://img.alexleo.click/Team-BoB_matplotlib_notes/title.jpg)